Five Security checkpoints for a connected car
Cyber security has become very crucial these days for connected car environment. The rate of connected car adaptation is simply not meeting the technology changes needed in terms of modern security benchmarking.
A Jeep hack made a lot of news last year where hackers were able to completely take control of Jeep remotely miles away from their home. It’s demonstrated live by the Wire magazine here.
A modern car is typically a computer controlled machine with dozens of ECUs (Electron Control unit) inside it.
Why the ECU security matters now than before?
In a connected car environment car ECUs gets connect to a network, security becomes important when someone is able to tap into your car ECUs remotely without physically present inside the car. Need for security obviously rises when security can be compromised remotely.
Because the car electronics was not born as internet connected data transmitting and receiving thing, the security might have been ignored in designing the ECUs which continues to be mostly designed like that today.
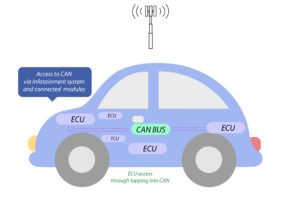
Back in days when the car didn’t connect to a network it was a good idea for a car’s critical systems to be built on a Controller Area Network (CAN) bus, but now the same CAN bus can be accessed through readily available ports such as an OBD2 port this can potentially act as a gateway to inside your car for a hacker/hacking device.
As modern day vehicles become more connected, they also risk becoming easier to access. Potential points of attack include:
- Maintenance interfaces: While it is possible to attack traditional IVNs directly through a vehicle’s maintenance interface, a shift to Ethernet/IP networks would make such attacks much easier for anyone with a laptop and basic hacking skills to execute
- Wi-Fi access points: Wi-Fi access points, if inadequately secured, offer hackers the chance to attack systems from anywhere within 10-15m of the vehicle.
- Cellular modems: Hackers can call a car’s cellular modem, and use audio signals to launch an attack.
- Car2x Wi-Fi: Frequently used to warn drivers approaching roadworks, Car2x Wi-Fi (based on the 802.11p standard) affords would-be attackers yet another way into a vehicle’s critical systems.
Areas where security can be employed in a connected car:
- ECU and tapping into CAN buses: ECU should not accept any data coming in without a TIM (Trusted Identity module). These could be vendor specific chips which could be embedded inside the existing ECU setup.
- OS and Firmware : Secure OS and Firmware to modern security standards
- Car Applications such as infotainment : What’s needed: Application Security rules
- Data privacy in connected car environment : Secure access to connected car data with encrypted telematics data push to servers
- Access Control: The connected car should connect to a network in a lock down mode – this means the cellular element such as GSM modem should be able to send the data to a predefined white listed server IP. This can be taken care at cellular network level.